“Just because you’re paranoid doesn’t mean that there isn’t somebody watching you”
That is a truism in this day and age. There has been much publicity about the Edward Snowden revelations and NSA’s PRISM and the Boundless Information programs. It has invited a lot of useful and needed public and private debate in the role of government and the tension between security and privacy. Some have stated that the PRISM program is not used for domestic crime fighting based upon claims by the Executive branch. It seems as if the Executive Branch tacitly concedes that if PRISM or Boundless Information programs were used for domestic crime fighting that it may be illegal and unethical and perhaps unconstitutional to do so. Some news agencies have reported on the DEA using information gathered from NSA programs for domestic crime solving (“Exclusive: U.S. directs agents to cover up program used to investigate Americans“) and in particular the derivative Special Operations Division (SOD) programs. This some people have dubbed this type of surveillance as “Trickle Down Surveillance.”
It has been well known for a long time that cell phone carriers retain information that can later be obtained by law enforcement concerning a certain cell phone. This information is almost always obtained by a search warrant.

But what can be done in real time?
What is the extent and capability of Big Brother and its tracking in real time?

The above look like cell phone towers. Are they all functional cell phone towers from industry or are they a method of domestic law enforcement warantless cell phone tracking and potential eavesdropping?
Perhaps.
There are many devises out there that can act as cell phone data “catchers.” They can be fixed or static cell phone looking towers. But there are also much more portable versions that are housed in vans, or hand-held or can be worn on one’s body:


To understand the forensics of cell phone tracking and potential eavesdropping one has to understand the basics of how a modern cell phone works. A carrier assigns a cell phone an International Mobile Subscriber Number (IMSI) or Temporary Mobile Subscriber Identity (TMSI) or the Electronic Serial Number (ESM). In an over simplified way this IMSI/TMSI/ESM is the manner in which your cell phone is differentiated from all other cell phones so you get your calls and not someone else’s. The most popular form of these devices are called “The Stingray.” Much like the Xerox company’s experience with its copier machines, the term Stingray is over-used in the community and has come to represent all similarly situated and capable devices. The term “Stingray” is trademarked by the Harris Corporation out of Florida and is one particular device. The Harris Corporation guards zealously the technical specifications and the capabilities of its devices.
What is known is this:
The IMSI/TMSI catcher devices act as a “Man in the Middle” style of intercept. In essence, your cell phone is almost constantly sending out signal in order to acquire cell phone tower coverage. The preference of your cell phone is to seek out the highest and best form of network which is going to be the 4G network ( A5/3 encryption or better). It so happens that the 4G network is better encrypted. If 4G is not available, it seeks 3G. And rarely, if 3G is not available, it will go to the old 2G network. The old 2G network is not well encrypted at all (A5/1 encryption). What the current version of IMSI catchers do is force a cell phone coverage area out of the better encrypted 4G and 3G networks, down to the 2G networks. Handsets that are artificially “stuck” in 2G will readily accept signals from other devices such as a Stingray or other IMSI catcher and a quasi-direction finder is then used to pin-point location.
So law enforcement, if they wanted, could seek the IMSI of TMSI or ESM information from the carrier of their particular target, the provider can then give general area and last use information to help narrow down the search, then the government would deploy a IMSI/TMSI catcher (such as a Stingray) in the area where the target is sought to be and then track in real time where the person is based upon this MITM style attack. It has been described by one user as “quite easy.”
Or in the alternative, if the government wanted, if there was a gathering, such as a demonstration or a riot, the same technology could be used to “grab” all of the IMSIs or TMSIs or ESMs in the area and then latter apply to carriers to determine who the subscribers are.
There is an upgrade to the original Stingray called “Stingray II” which enables the Stingray to work on 3G and 4G networks now as the 2G network will no longer be supported.
Other similar tactics can be used for Denial of Service (DoS) style attacks where a device, such as the Harris Corporation Gossamer 4000 device (it can both track IMSI and also push a DoS attack) can be used to possibly “jam” a particular cell phone or all cell phones in an area.

Another platform known as “FishHawk,” (PDF) is reported to be able to eavesdrop in real time the conversations that happen. There are reports of software/hardware called “Triggerfish” which can eavesdrop in real time as well. “Porpoise” (PDF) is designed to be installed on a laptop and is reported to be able to intercept text messages in real time.
There is a proliferation of these types of devices. How frequently they are being used is not known as most state’s guard the very possession and deployment of these devices greatly. They are frequently protected against FOIA or FOIA like disclosures because of their sensitive nature. According to the ACLU in its report “How the Government Is Tracking Your Movements” there are at least 15 states that have this capability.
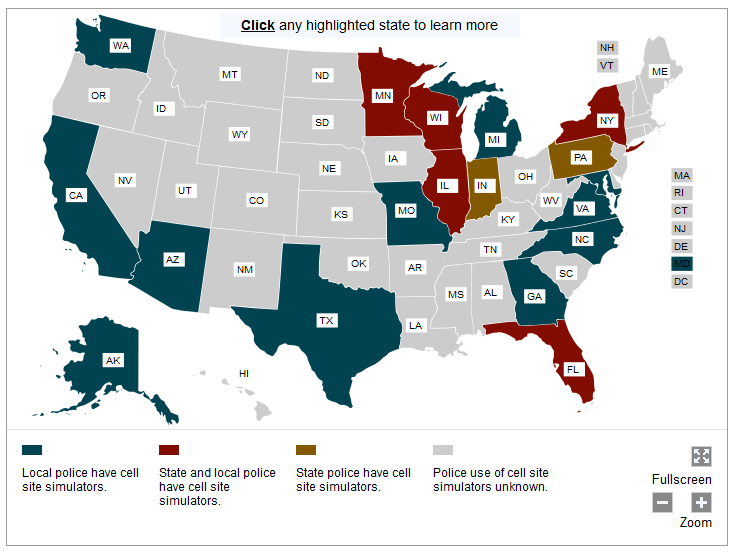 The Pennsylvania State Police have purchased a Stingray and Stingray II according to the Declaration who posted these purchase orders and receipts for the Stingray and Stingray II upgrades. It is unknown how or if it is used.
The Pennsylvania State Police have purchased a Stingray and Stingray II according to the Declaration who posted these purchase orders and receipts for the Stingray and Stingray II upgrades. It is unknown how or if it is used.
Without a doubt, there are constitutional issues surrounding the use of these types of devices in domestic crime fighting. In at least one case, the issue has come to a head. In State of Florida v. James L Thomas, 2008-CF-3350A there was a suppression hearing based upon the use of this technology.What is very revealing in the suppression hearing was what an officer explained under oath. He said that he “quite literally stood in front of every door and window” with his stingray to track the phones inside a large apartment complex.

and later the officer states:



